What Is AWS Config?
AWS Config is the service that enables you to assess, audit and evaluate the configurations of your AWS resources automatically. It enables you to automate the evaluation of recorded configuration against desired configuration using features called AWS config rules. For example your requirement is all S3 bucket created is encrypted. You can deploy AWS config manage rule that automatically evaluates your S3 bucket resource the moment its created or modified. AWS provides some rich set of rules that evaluates some of the common scenarios and those are called manage rules but you also have ability to create your own custom rules using AWS lambda.
Features
Track state of all resources(OS level too — Windows/Linux)
Meet your compliance need(PCI-DSS, HIPAA)
Validate against AWS Config Rule
Setting up AWS Config

* All resources: You can check on, Record all resources supported in this region
OR
Global resources like IAM
OR
We can even check specific resources eg: EC2* Amazin S3 bucket: This bucket will receiv configuration history and configuration snapshot files
* Amazon SNS topic(Optional): We can send config changes to S3 bucket
* AWS Config role: It give AWS config read-only access(IAM Role)to AWS resource
NOTE: AWS Config is a regional resource, so in case if you want to track resources in every region, you need to configure it in every AWS region. Please make Include Global Resource like IAM is only checked in one region otherwise you will get duplicate resources that is recorded and tracked within AWS config.
- After clicking all the details, select Next at the bottom of the screen.
* Skip AWS Managed Rules this for the time being
On the Review screen click Confirm.
You will see the AWS Config page like this

- In the last section we have skipped the Rules. Rules allow you to setup a rules that will then check a specific rule evaluation against your AWS resources to make sure it’s at a desired configuration state.AWS config has two types of rules
AWS managed rule: These are config rule managed by AWS
Custom lambda rule:
Custom rule using Guard
In order to add a rule, Click on Rules and then Add rule

- In the search bar search for volume and then select ec2-volume-inuse-check. This will check if EBS volumes are attached to EC2 instance. This is useful in cases to save cost and cleanup all the EC2 volume which is not attached to any EC2 instance(Just to be on the safer side in case of production environment, it’s always a good idea to take the snapshot before cleaning up any volumes).

- Keep all the settings as default and click on Next at the bottom of the screen.
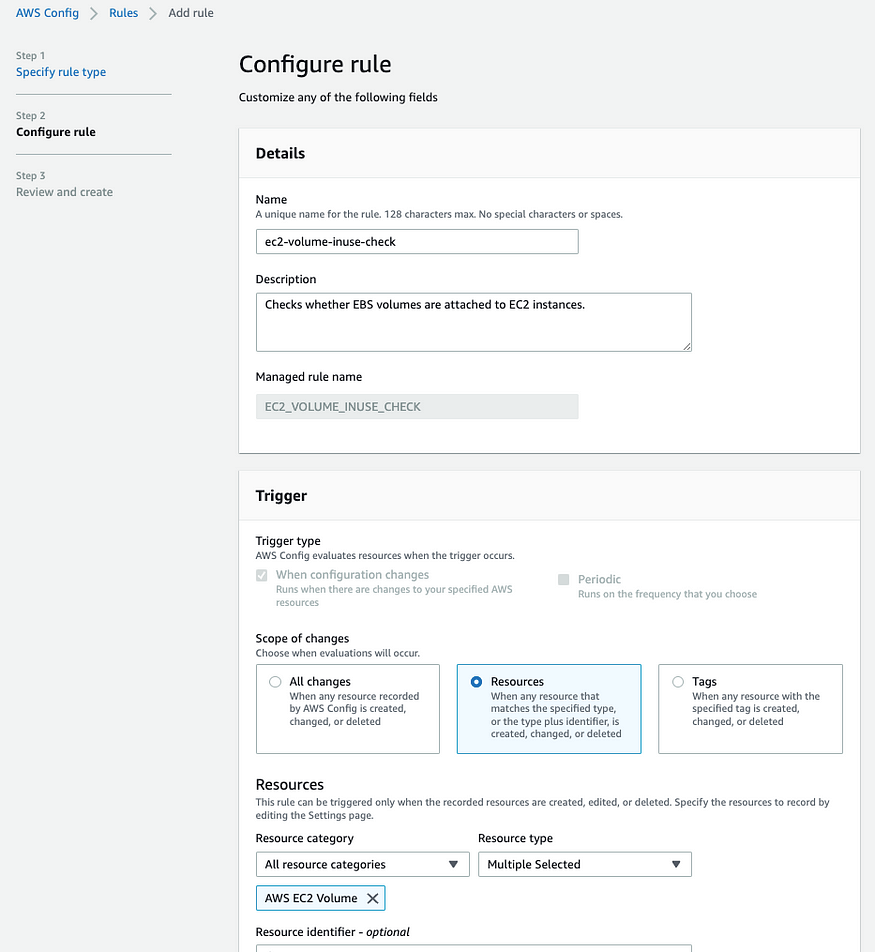
In the next screen, click on Add rule.
For the purpose of demo, go to the EC2 console us-east-1.console.aws.amazon.com/ec2, click on Volumes and then Create volume

- Click 1 GB Volume, by modifying the Size to 1 and click on Create volume. Don’t attach this volume to any instance.

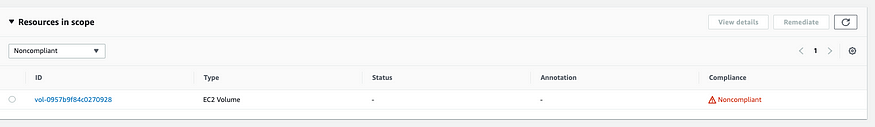
- Go back to AWS config, click on rule we have created and Actions drop-down select Re-evaluate.

- Once the re-evaluation is done, you will see one non-compliant resource.

- If you click on the rule itself, you can further drill down to see which resource is in non-compliant state. This is the volume we have just created and because its not attached to any EC2 instance its in non-compliant state